Tell Your Friends: How to Protect Yourself from Android's Biggest Security Flaw in Years
Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.To be clear, Zimperium is a security firm, so their main goal in discovering this vulnerability was to gain a little notoriety while helping Android manufacturers and developers plug up a potentially disastrous security risk. Nonetheless, the general basis for the attack is now public knowledge, so hackers with malicious intents need only to reverse-engineer some of the finer aspects of this exploit before they can actually start putting it to use.
How It WorksThe premise is relatively simple—an attacker only needs your phone number to take total control of your Android device by sending an MMS with the malicious code embedded in it. This means that, theoretically, a hacker could send you an MMS message while you were asleep, take control over your phone, then remove all traces of the attack while you remained none the wiser.Once the trojan file has been sent over MMS, the attacker can read your messages, retrieve your login credentials for various sites and services, operate your device's microphone, and access almost any file stored on your phone. To put it simply, a hacker could potentially gain access to all of the sensitive data stored on your smartphone by sending you a simple picture message. Android devices can be hacked with a single MMS message.
What Devices Are Affected?This particular attack exploits a security loophole in Android's media library (Stagefright) to gain escalating permissions. Since Stagefright has been the default media library in Android devices for the past 5 years, this exploit has the potential to compromise almost any phone running Android 2.2 (Froyo) through Android 5.1.1 (Lollipop).
When Is a Fix Coming?Google has already added a fix for the Stagefright exploit to Android's code base, but this certainly doesn't mean that we're in the clear.Consider the way Android updates usually work: First, Google adds new code to AOSP (which they've already done in this case). Then, Google pushes this updated version out to manufacturers like Samsung or HTC. The manufacturers then spend months adding their own custom tweaks to the firmware before sending it out to the cellular carriers. The carriers then spend another few months adding their own bloat to the firmware, and ultimately, the security fix is sent out to end users about 6 months after it was originally made.It certainly won't take hackers a full 6 months to replicate this exploit, so in the meantime, we'll need to take matters into our own hands.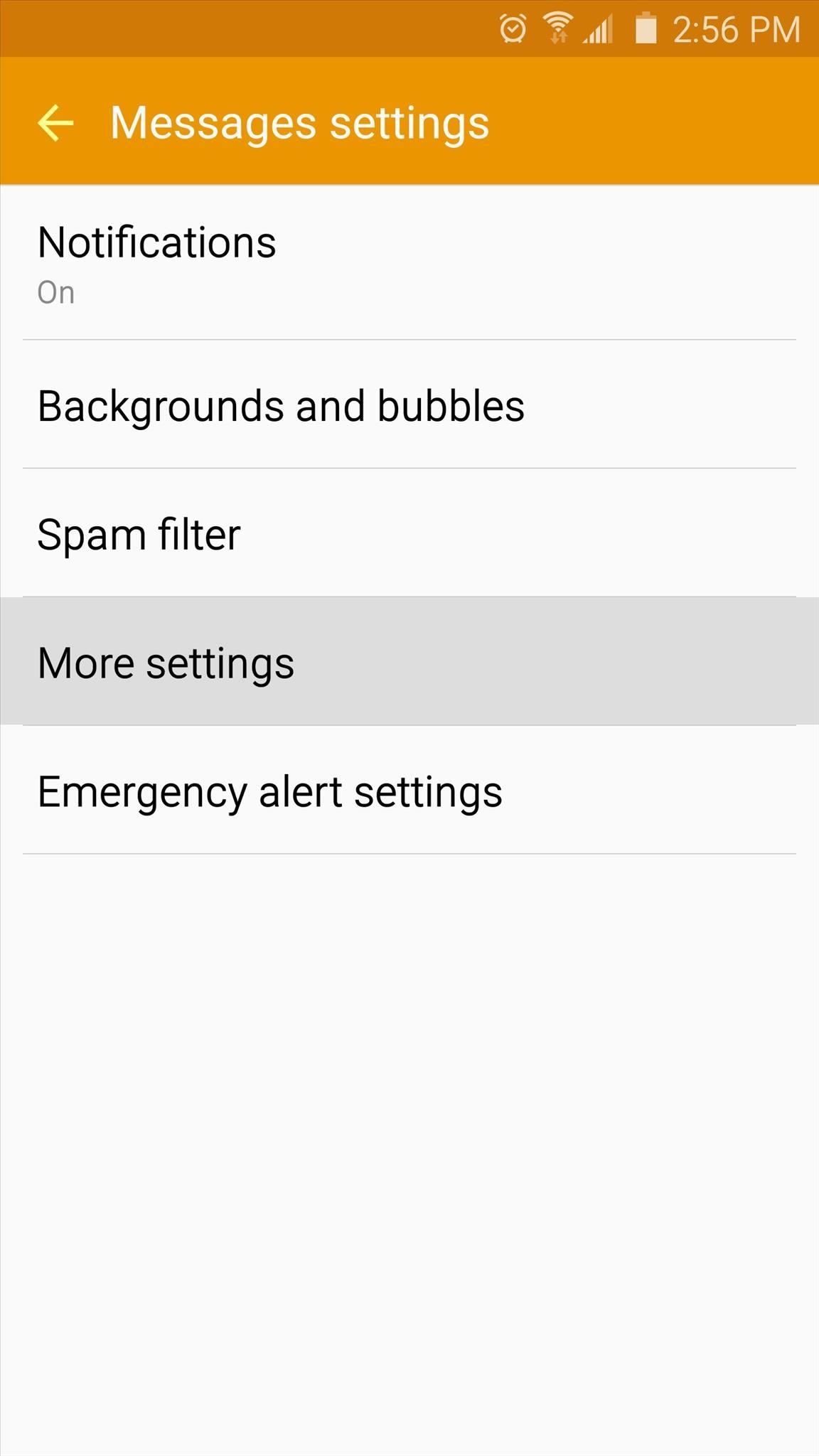
Disable MMS Auto-Retrieve to Prevent AttacksSince the exploit works by sending an MMS that is automatically downloaded by your phone, the only way to prevent this attack is to set your phone to not automatically download MMS messages. The drawback here is that you'll have to tap future MMS messages to download them manually, but it's a small price to pay for security.The process will vary depending on your text messaging app, but I'll outline it for some of the most popular messaging apps below.Samsung Messages App:If you're using the default Messages app on a Samsung device, start by heading to the Settings entry in app's main menu. From here, select "More settings," then "Multimedia messages." Finally, disable the "Auto retrieve" option to ensure that potentially dangerous MMS messages are not automatically downloaded. Google Messenger App:With the Google Messenger app, start by tapping the three-dot menu button in the app's top-right corner, then select the Settings entry. From here, choose Advanced, then make sure the "Auto-retrieve" option is disabled on the next screen. Hangouts App:To disable MMS auto-retrieve in the Hangouts messaging app, head to the side navigation menu and select Settings. Next, choose the SMS entry, then scroll down a bit, and make sure that the "Auto retrieve MMS" option is disabled. From now on, your phone will no longer download MMS messages automatically, meaning the exploit can't be triggered on your phone without your knowledge. But you should still be very careful about opening MMS messages, and in general, do not open an MMS message that came from a phone number you don't recognize.Personally, I think this exploit shines a light on Android's convoluted update process, because without the manufacturers and carriers meddling around with our phones' firmware, we could already have a fix for this issue sent directly from Google. What are your main concerns with the Stagefright exploit? Let us know in the comment section below, or drop us a line on Android Hacks' Facebook or Twitter, or Gadget Hacks' Facebook, Google+, or Twitter.
You can also turn Low Power Mode on and off from Control Center. Go to Settings > Control Center > Customize Controls, then select Low Power Mode to add it to Control Center. When Low Power Mode is on, your iPhone will last longer before you need to charge it, but some features might take longer to update or complete.
[Discussion] Would you be interested in a power menu with
Once you set this feature up, you can skip the fingerprints scanning when you want to unlock your Samsung Galaxy. Therefore, you can access your smartphone without too much hurdle. I hope these tips on how to make Samsung Galaxy Fingerprint scanner work faster helps you save time and energy in unlocking your smartphone.
How to make fingerprint scanner work faster on Your - YouTube
When you upload pictures to Facebook, there are a lot of things that can cause problems if you are not familiar with its system. Troubleshooting these problems involves determining the size of the
Upload: How to Upload Photos - support.shutterfly.com
I've been trying to find out how to kill/turn-off cellular radio (on a rooted device) using some command on ADB. My research only found that I should either (using GUI) enable Airplane Mode, or typ
Now's The Time - watch face for smart watches Download For PC
What to do about traffic signals that ignore motorcycles in the pavement at a red light to trigger the sensor. to traffic lights so they change to green. If
Trigger Green Traffic Lights | Bit Rebels
Nov 25, 2017 · Years after it first took over the planet and introduced millions, if not billions, of people to K-pop music, Psy's "Gangnam Style" has finally reached three billion views on YouTube, the
PSY- Gangnam Style (Official Music Video) - YouTube
Turn the classic 70's wireless toy into a modern high-tech spy device. Hey, he never picked up any chicks with it anyway. Mr. Microphone Hack! Uploaded 06/14/2008
How to Properly use wireless microphones - WonderHowTo
Giving yourself root access will let you have superuser status on your B&N Nook eReader. Make sure your reader is on airplane mode, then connect it to your computer and follow the steps outlined in this tutorial to gain root access to your reader.
How to Use Trook on your Barnes & Noble Nook eBook reader
Siri will then ask you how to pronounce the contact's first name. Say the name correctly. Siri will offer you four pronunciation options to choose from. Select the one that is the correct Siri pronunciation. If none of the options are close enough, tap Tell Siri, "Again," to repeat the process until you get a Siri pronunciation you like.
Teach Siri to Correctly Recognize and Pronounce Names in Your
How to Automate Proper Source Citation Using the APA, MLA, or
The photo-collage app Layout from Instagram, which was launched for iPhone in March this year, has finally reached the Android platform.. The app features the same design as seen in its iOS app
Layout from Instagram: Collage - Apps on Google Play
0 comments:
Post a Comment